Client-side Analytics and MIXR
What is Client-side Analytics?
Global Valuation research has created a new architecture for secure, data privacy respecting analytics. We call it Client-side Analytics, as the analytics cannot expose any private data that the data owner does not agree to be shared with the author of the analytics. A Blockchain technology can be used as the underlying data platform for smart contract-based Client-side Analytics.
Client-side Analytics is a safe way for data owners to allow published analytics to be run on their private data, such as banking or hedge fund portfolios. This approach will have many use cases beyond Financial Services. We illustrate here some use cases that will change how analytics are used in finance.
How Client-side Analytics Works
Analytics which are calculated on a contract portfolio details of which cannot be directly accessed by the initiator of the calculation.

Use Cases for Client-side Analytics
Addressing Wrong-way Risk (WWR) is a very high regulatory priority, as demonstrated by the new, comprehensive WWR regulation proposal from the BCBS: Guidelines for counterparty credit risk management. WWR is intractable with current tools, it requires a technological solution to bridge the data asymmetry between counterparties. The Market Infrastructure for Client-side Risk (MIXR) will provide that solution, along with the Esther risk analytics that enable the global roll-out of MIXR at a low cost.
Other MIXR use cases include:
-
Client-facing trading and structuring applications at dealers including full client portfolio optimisation
-
Capital and collateral optimisation strategies on an inter-dealer basis
-
Cross-margining strategies between Clearing Houses
-
The accurate calculation of collateral add-ons for wrong way risk, leading to a global reallocation of collateral requirements that will substantially reduce systemic risk without changing total posted amount
-
Direct, regulator driven execution of risk analytics on the portfolio of market participants (and regulators have multiple paths to incentivise the use of MIXR by allowing collateral and capital savings at the condition that risk mitigation is established)
Market Infrastructure for Client-side Analytics
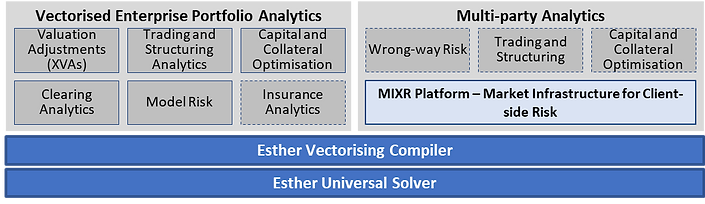
The MIXR platform will be the first risk analytics platform to support distributed multi-party workflows and the tokenization of analytics. Esther enables MIXR through the power of its vectorising compiler, which gives is an orders of magnitude quality, performance and cost advantage over traditional stochastic calculus-based models.
Esther's core capability is to define and execute vectorised portfolio analytics at the enterprise scale, across all asset classes and use cases. With the addition of MIXR, multi-party analytics become possible.
Esther and the MIXR Platform:
Use Cases
The MIXR infrastructure will provide the necessary secure messaging, authentication and portfolio validation services for Client-side Analytics. MIXR will have jurisdictional scope and context, with each jurisdiction utilising the same underlying software for the local instance of MIXR.
MIXR's messaging is based on the Smart Trade Esther Messages standard, described in detail on the Architecture page.
This video presentation given an overview of MIXR and its key use cases.
